Citizen Lab developed a new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations.
Between August 2016 and August 2018, Citizen Lab scanned the Internet for servers associated with NSO Group’s Pegasus spyware. They found 1,091 IP addresses that matched their fingerprint and 1,014 domain names that pointed to them. They developed and used Athena, a novel technique to cluster some of the matches into 36 distinct Pegasus systems, each one which appears to be run by a separate operator.
Israel-based “Cyber Warfare” vendor NSO Group produces and sells a mobile phone spyware suite called Pegasus.
To monitor a target, a government operator of Pegasus must convince the target to click on a specially crafted exploit link, which, when clicked, delivers a chain of zero-day exploits to penetrate security features on the phone and installs Pegasus without the user’s knowledge or permission.
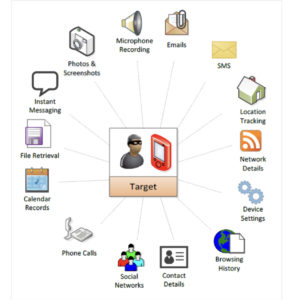
Once the phone is exploited and Pegasus is installed, it begins contacting the operator’s command and control (C&C) servers to receive and execute operators’ commands, and send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls from popular mobile messaging apps.
The operator can even turn on the phone’s camera and microphone to capture activity in the phone’s vicinity.
Pegasus exploit links and C&C servers use HTTPS, which requires operators to register and maintain domain names.
Domain names for exploit links sometimes impersonate mobile providers, online services, banks, and government services, which may make the links appear to be benign at first glance.
An operator may have several domain names that they use in exploit links they send, and also have several domain names they use for C&C.
The domain names often resolve to cloud-based virtual private servers rented either by NSO Group or the operator. The front-end servers appear to forward traffic (via a chain of other servers) to servers located on the operator’s premises.
The study found suspected NSO Pegasus infections associated with 33 of the 36 Pegasus operators we identified in 45 countries: Algeria, Bahrain, Bangladesh, Brazil, Canada, Cote d’Ivoire, Egypt, France, Greece, India, Iraq, Israel, Jordan, Kazakhstan, Kenya, Kuwait, Kyrgyzstan, Latvia, Lebanon, Libya, Mexico, Morocco, the Netherlands, Oman, Pakistan, Palestine, Poland, Qatar, Rwanda, Saudi Arabia, Singapore, South Africa, Switzerland, Tajikistan, Thailand, Togo, Tunisia, Turkey, the UAE, Uganda, the United Kingdom, the United States, Uzbekistan, Yemen, and Zambia.
Pegasus also appears to be in use by countries with dubious human rights records and histories of abusive behaviour by state security services. In addition, it was found indications of possible political themes within targeting materials in several countries, casting doubt on whether the technology is being used as part of “legitimate” criminal investigations.
In a separate report, Communications surveillance is being carried out by Kenyan state actors, essentially without oversight, outside of the procedures required by Kenyan laws.
Intercepted communications content and data are used to facilitate gross human rights abuses, to spy on, profile, locate, track – and ultimately arrest, torture, kill or disappear suspects, as this report documents. The Kenyan constitution guarantees freedom from torture, cruel, inhuman and degrading treatment and the right to a fair trial as fundamental rights.
These abuses have marred Kenya’s counterterrorism operations and further eroded Kenyans’ already weak trust in the agencies responsible for protecting them. The investigation also explored the potential impact of unaccountable communications surveillance on the 2017 election cycle.
The National Intelligence Service (NIS) regularly shares information with police agencies, some of whom have been engaged in gross human rights abuses, according to multiple independent media, civil society, and Kenya National Commission on Human Rights (KNHCR) investigations. The NIS appears to have direct access to communication networks across Kenya.
This direct access means that the network operator itself has little to no knowledge of the interception of communications occurring on its network, and therefore no real ability to check these powers or report the potentially abusive use of communications surveillance powers.
Kenya Insights allows guest blogging, if you want to be published on Kenya’s most authoritative and accurate blog, have an expose, news TIPS, story angles, human interest stories, drop us an email on [email protected] or via Telegram

 Investigations2 weeks ago
Investigations2 weeks ago
 Investigations2 weeks ago
Investigations2 weeks ago
 Investigations2 weeks ago
Investigations2 weeks ago
 Investigations1 week ago
Investigations1 week ago
 Opinion2 weeks ago
Opinion2 weeks ago
 Investigations1 week ago
Investigations1 week ago
 Investigations1 week ago
Investigations1 week ago
 Business1 week ago
Business1 week ago