Investigations
The Hidden Hand: How Telegram’s Infrastructure Links to Russian Intelligence
At the center of this revelation is Vladimir Vedeneev, a 45-year-old Russian network engineer with an outsized—and previously hidden—role in Telegram’s operations.

Damning Investigation Reveals Critical Security Vulnerabilities in World’s Most Popular “Secure” Messenger
An OCCRP investigation exposes how the man controlling Telegram’s network infrastructure has deep ties to Russia’s FSB intelligence service
For over a billion users worldwide, Telegram represents the gold standard of secure messaging. Pavel Durov, the app’s enigmatic founder, has cultivated an image as a digital freedom fighter who fled Russia to protect user privacy, famously declaring that Telegram has “never disclosed a single byte of private messages” in its 12-year history.
But a bombshell investigation by the Organized Crime and Corruption Reporting Project (OCCRP) has shattered this carefully constructed narrative, revealing a web of connections between Telegram’s critical infrastructure and Russian intelligence services that threatens the privacy of users globally.
The Man Behind the Network
At the center of this revelation is Vladimir Vedeneev, a 45-year-old Russian network engineer with an outsized—and previously hidden—role in Telegram’s operations.
Court documents obtained by OCCRP reveal that Vedeneev’s company, Global Network Management (GNM), controls over 10,000 IP addresses for Telegram and maintains exclusive access to the messenger’s servers.
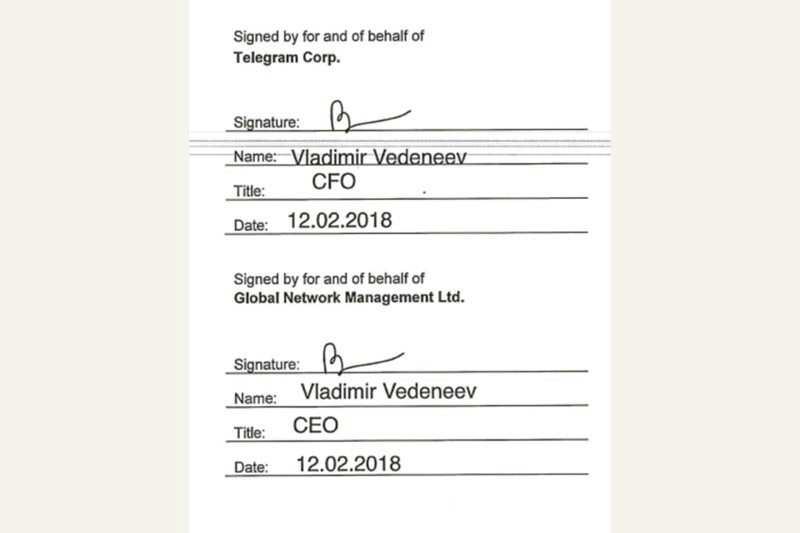
What makes this relationship particularly troubling is not just its scope, but its secrecy. According to the investigation, Vedeneev was empowered to sign contracts as Telegram’s Chief Financial Officer—despite having no publicly known connection to the company.
A contract found in Florida court records shows Vedeneev signing documents in dual roles: once as GNM’s director and again as Telegram’s CFO.
“Neither Elies Campo, a former partnership development manager with Telegram who spoke with reporters, nor others familiar with Telegram’s corporate structure, have ever heard of Vedeneev,” the OCCRP report notes—a striking revelation given Telegram’s already secretive corporate culture.
The Russian Connection
While there’s no evidence that Vedeneev’s current company has directly cooperated with Russian authorities, the investigation reveals deeply concerning connections through his other business ventures.
Vedeneev is the founder of GlobalNet, a major Russian telecommunications operator that controls 18,000 kilometers of backbone infrastructure spanning from Siberia to Western Europe.
Among GlobalNet’s clients are some of Russia’s most sensitive organizations:
- The FSB intelligence agency – Russia’s primary domestic security service
- GlavNIVTS – A secretive “research computing center” that helped plan the invasion of Ukraine and developed tools to deanonymize internet users
- The Kurchatov Institute – A flagship state-owned nuclear research laboratory sanctioned by the United States
Perhaps most alarmingly, internal accounting documents from 2024 show that another Vedeneev company, Electrotelecom, lists the FSB as one of its most important government clients, installing and managing surveillance equipment for FSB offices in St. Petersburg and the Leningrad region.

The Technical Vulnerability
The implications of these connections become clearer when examining how Telegram’s encryption actually works. Unlike popular belief, security experts warn that even Telegram’s end-to-end encrypted chats leave users vulnerable to tracking by anyone who can monitor network traffic.
Michał “Rysiek” Woźniak, a security specialist who formerly worked for OCCRP, explains the critical weakness: Telegram’s MTProto protocol attaches an unencrypted element called “auth_key_id” to each message. This identifier makes it possible to track specific user devices, even when message content remains encrypted.
“If I know your device’s ‘auth_key_id,’ and I can listen in on the network that handles the data… I know it is your specific device communicating with Telegram servers,” Woźniak explains. “By looking at the network packets… I also get your IP address at a given time, which tells me your rough geographic location.”
This means that whoever controls Telegram’s network infrastructure—in this case, companies with proven ties to Russian intelligence—may be able to conduct what experts call “metadata surveillance,” tracking user locations, communication patterns, and device identifiers even without reading message content.
A Pattern of Deception
The investigation also exposes significant inconsistencies in Durov’s public statements. While he has repeatedly claimed never to have visited Russia since leaving in 2014, leaked FSB data revealed that Durov had traveled to Russia more than 50 times between 2015 and 2021.
This pattern of deception extends to Telegram’s infrastructure claims. Despite Durov’s assertions that Telegram has no infrastructure in Russia, the OCCRP investigation reveals that until 2020, the IP addresses now managed by Vedeneev’s Antigua-based company were previously controlled by his Russian firm GlobalNet.
The Geopolitical Context
These revelations come at a particularly sensitive time. Durov was arrested in France in August 2024 on charges related to illegal content circulation on Telegram, highlighting growing Western concerns about the platform’s role in facilitating criminal activity.
Meanwhile, Telegram’s relationship with Russian authorities remains murky—the app was banned in Russia in 2018 for refusing to hand over encryption keys, but the ban was lifted in 2020 after Telegram agreed to “help with extremism investigations”.
Ukrainian intelligence officials have been particularly vocal about these concerns. Ukrainian officials confirmed in 2023 that “The FSB, and only them, have the keys to Telegram”, warning that the service is being used for espionage purposes.
The Human Cost
For millions of users who rely on Telegram for sensitive communications—from journalists and activists to ordinary citizens in authoritarian regimes—these findings represent a fundamental betrayal of trust.
John Scott-Railton, a Senior Researcher at The Citizen Lab, warns of the real-world implications: “When people don’t know what is actually going on, but assume they have metadata privacy, they can unknowingly make risky choices, bringing danger to themselves and the people they’re communicating with. This is doubly true if the Russian government sees them as a threat.”
A Ukrainian IT specialist, speaking anonymously to reporters, described how Russian forces have used “man-in-the-middle” surveillance after capturing network infrastructure: “In such an attack, the hackers aren’t even interested so much in the user’s correspondence. They get metadata to analyze. And that means IP addresses, user locations, who exchanges data packets with whom… really, all possible information.”
The Broader Implications
This investigation raises fundamental questions about the security of communications infrastructure in an increasingly connected world. While Telegram markets itself as a secure alternative to services like WhatsApp, the reality appears far more complex.
The revelation that critical infrastructure for a billion-user messaging service is controlled by individuals with demonstrated ties to intelligence services represents a new category of cybersecurity threat—one that operates not through hacking or data breaches, but through the very architecture of digital communications.
Woźniak, the security expert, summarized the gravity of the situation: “If someone has access to Telegram traffic and cooperates with Russian intelligence services, this means that the device identifier becomes a really big problem—a tool for global surveillance of messenger users, regardless of where they are and what server they connect to.”
Unanswered Questions
As this investigation continues to reverberate through the cybersecurity community, several critical questions remain unanswered:
- How long have Russian intelligence services potentially had access to Telegram’s metadata?
- What other messaging services might be vulnerable to similar infrastructure-based surveillance?
- Why did Telegram grant such extensive access to individuals with clear intelligence service connections?
- What safeguards, if any, exist to prevent the abuse of this access?
Neither Durov nor Vedeneev responded to requests for comment from OCCRP investigators, leaving users to grapple with the implications of potentially compromised communications.
The Path Forward
For users concerned about the security of their communications, this investigation serves as a stark reminder that true digital privacy requires more than marketing promises and encryption protocols. It demands transparency about infrastructure, ownership, and the potential for surveillance at every level of the communications stack.
As governments worldwide grapple with the balance between security and privacy in digital communications, the Telegram case demonstrates that the greatest threats to user privacy may not come from authoritarian overreach or criminal hackers, but from the very companies and individuals we trust to protect our digital lives.
The billion users who rely on Telegram for secure communications deserve answers—and the right to make informed decisions about their digital security based on facts, not fiction.
This investigation was conducted by OCCRP’s Russian partner, Important Stories, with additional reporting by Roman Anin and Nikita Kondratyev. Technical analysis was provided by security specialist Michał “Rysiek” Woźniak.
Kenya Insights allows guest blogging, if you want to be published on Kenya’s most authoritative and accurate blog, have an expose, news TIPS, story angles, human interest stories, drop us an email on [email protected] or via Telegram
-

 Grapevine2 weeks ago
Grapevine2 weeks agoAlleged Male Lover Claims His Life Is in Danger, Leaks Screenshots and Private Videos Linking SportPesa CEO Ronald Karauri
-

 Grapevine1 week ago
Grapevine1 week agoRussian Man’s Secret Sex Recordings Ignite Fury as Questions Mount Over Consent and Easy Pick-Ups in Nairobi
-

 News5 days ago
News5 days agoTHE FIRM IN THE DOCK: How Kaplan and Stratton Became the Most Scrutinised Law Firm in Kenya
-

 Investigations7 days ago
Investigations7 days agoMulti-Million Dollar Fraud: Three Kenyans Face US Extradition in Massive Cybercrime Conspiracy
-

 Economy6 days ago
Economy6 days agoIran Demands Arrest, Prosecution Of Kenya’s Cup of Joe Director Director Over Sh2.6 Billion Tea Fraud
-

 Business6 days ago
Business6 days agoA Farm in Kenya’s Rift Valley Ignites a National Reckoning With Israeli Investment
-

 Africa1 week ago
Africa1 week agoFBI Investigates Congresswoman Ilhan Omar’s Husband’s Sh3.8 Billion Businesses in Kenya, Somalia and Dubai
-

 Business2 weeks ago
Business2 weeks agoM-Gas Pursues Carbon Credit Billions as Koko Networks Wreckage Exposes Market’s Dark Underbelly

















