Sci & Tech
How Forkbombo, Kenya’s most Lethal Hackers Group was formed by a DCI Officer and how it has since mutated in Africa.

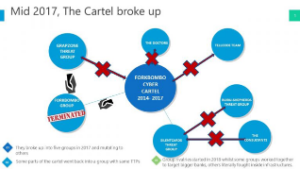
A cyber threat group – Forkbombo that caused chaos in the financial sector due to coordinated heists was taken down in Kigali late 2019.
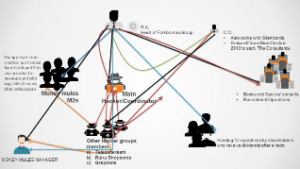
This group flourished for several years after the main Cyber Cartel was taken down in 2017, with the third in command assuming Operational Command, after he unsuccessfully was unable to attain a Political statue during 2017 nominations, thus quickly reverting to crime, and organizing this threat group with use of Cut-Outs across its organized crime operations, such that even the Money Mules didn’t know each other and could not have access to the hackers’ deployed to run target penetrations.
There have been several other cases of hacking in the past, with estimates of over 2 billion shillings being lost through black hat operations annually. Some investigations have led to arrests though no convictions have been made so far.
In most cases, the suspects find their way out through cash bails and out of court settlements. The hackers formed a syndicate, one which has continued to cause havoc. As a team, they have managed to stay a step ahead, beating the security agencies and cyber forensic specialists. Banks have kept the attacks secret on purpose.
Forkbombo was given this name because during 2016 to 2017, they used [email protected] to receive keylogger data after infecting a machine with the keylogger variant that they wrote in-house. Known to few, is that the mastermind behind the the group was actually a DCI officer who colluded with hackers group he was assigned to investigate and put on record. He decided to preach water and drink wine.
In the emergence of tremendous cyber security hitch – hacking incidences in Kenya in 2010, the Directorate of Criminal Investigations (DCI) received many reports of companies and individuals who had lost money or crucial information to hackers. in the financial sphere.
The reports were becoming overwhelming to DCI, which had few experts in the field of cyber crime technology to resolve the cases.However, one officer was exceptional, Mr Calvin Otieno Ogalo. He, among other officers, was tasked to investigate and resolve the cases as soon as possible to minimize the backlog and serve justice to the victims and most importantly track and arrest the hackers.
According to reports, Mr Ogalo was so good that by 2012 he had concluded almost all his investigations and had names of the best cybercriminals in the country. However, instead of bringing them to book as was required of him, he instead organised them into a lethal cybercrime gang that would hack institutions and individuals seamlessly, stealing either money or crucial information.
He was discovered later, which led to his silence and unceremonious exit from the DCI as a crimebuster in 2013. Nothing much about his exit or the gang he had formed was reported then – kept as a secret to control public outrage.
In his gang that later would be named Forkbombo was Mr Alex Mutungi Mutuku, one of the best hackers in the country. Others included Reuben Kirogothi Mwangi, Eric Dickson Njagi, Godfrey Gachiri, Erickson Macharia Kinyua and Stanley Kimeu Mutua.
Mr Ogalo roped in the services of insiders in targeted institutions and on top of it former Kenya Revenue Authority officers Edward Kiprop Langat, David Wambugu, Albert Komen and James Mwaniki. Also in the gang were Henry Achoka, Duncan Bokela and Martin Murathe.
Investigations by cybersecurity group OnNet Africa found an email associated with the hackers in almost every hacking incidence, [email protected].
One of the group’s major hits was in 2013 when they infiltrated the Judiciary’s system and requested National Treasury to approve Ksh80 million payment to several fictitious companies. The payments would be flagged by CFC Bank (now Stanbic) which called Judiciary’s chief of finance Mr Benedict Omollo, but the money was already gone. Later, Mr Achoka, Mr Bokela, Mr Mwangi and Mr Murathe of the Forkbombo group would be arrested and convicted seven years later, in January 2020.
One of the masterminds of the heist, Mr Mwangi, is currently serving a jail term in Rwanda alongside seven other Kenyans after attempting to Equity Bank in Kigali.
The Judiciary heist was neither the first nor the last, as the group would target other institutions, sometimes succeeding and other times being arrested. To them, being arrested was part of their job and they would pay cash bail and get back to work. For instance, in 2014, Mr Mutuku and Mr Stanley Kimeu Mutua were arrested after hacking into NIC Bank and stealing crucial information and Ksh2.88 million. In this incident, they were demanding a total of 200 bitcoins (equivalent to Ksh6.2 million then) in exchange for the information. The duo were released on Ksh700,000 cash bail.
In three months’ time, Mr Mutuku was accused of infiltrating the Safaricom system and stealing airtime worth Ksh3.6 million. Most probably he found a loophole in the Safaricom system, and a month later, it is alleged that Mutuku tricked the system to recharge his phone number with Ksh20,000 airtime.
Forkbombo is believed to have stolen at least Ksh400 million between 2013 and 2017. though the amount could be higher than that. It is believed that Forkbombo hacked and stole at least Ksh50 million from the Kenya Police Sacco in 2017.
The Kenya Police Sacco heist was so easy for them, and now they decided to loot KRA, through the help of two American nationals, Larry Peckham II and Denise Huitron, who were in constant communication with Mr Ogalo and even visited the country at one time.
In the heist where the taxman is said to have lost at least Ksh3.9 billion, Mr Edward Kiprop Langat (former KRA employee) is said to have been used to plant a laptop in the KRA servers. Other suspects of the heist are Mr Mutuku, Mr Langat, Mr Wambugu, Lucy Katilo Wamwandu, Kenneth Opege Riaga, James Mwaniki, Gilbert Kiptala Kipkechem and Joseph Kirai Mwangi.
Forkbombo, through Mr Mwangi recruited more suspected hackers including Dedan Muchoki Muriuki, Samuel Wachira Nyuguto, Damaris Njeri Kamau and Steve Maina Wambugu. Also a Ugandan and at least three Rwandans were recruited even as the group sought to create a hacking software, according to intelligence reports.
In 2016, Forkbombo is believed to have merged with another group of hackers, Grapzone, which had since 2013 been targeting supermarkets.
In another group is – SilentsCards, a home grown cyber cartel which sprung from Forkbombo Group which terrorised local banks in 2016 and 2017 before being quelled by a multi-agency team of experts from Kenya Revenue Authority, Banking Fraud Unit and Cyber Crime Unit.
According to Poland based cybersecurity firm OnNet, the SilentCards started robberies late 2017, inheriting the old version key logger used by Forkbombo and perfected it for collection of key logger data in a targeted environment.
Report shows that that just like Forkbombo group, SilentCards also targeted information servers, copy and evaluate audit reports to plan future attacks. After collecting as many credentials as they could, those hackers moved Sh400 million in batches, crediting fictitious accounts, then accessed either via VISA/MasterCard overseas or with use of Mobile Money Transfers.
Unlike Forkbombo which has several money mules, SilentCards relies a lot on foreigners for quick transactions outside the country. Those hackers are known to specialize in python scripts to create quick tools for exploitation phase of an environment.
They are also known to use opensource tools like Empire, Metasploit, DeathStar, Bloodhound, CrackMapExec, Aesshell, XmultiShell, CHAOS and Katoolin.
It is believed that SilentCards joined with upshot GrapZone late last year to regroup into Forkbombo.
According to a report by Group iB, one of the top global providers of cyber security solutions, Kenya is emerging as one of the thriving hubs for cyber crime in the world. “Currently, only five groups pose a real threat to the financial sector; Cobalt, Silence, MoneyTaker (Russian), Lazarus (North Korea), and SilentCards (a new group from Kenya),” explained the security firm in its 2019 High-tech Crimes report.
Group iB has been conducting threat analysis for the last 17 years and says SilentCards is known for attacks on ATMs and card processing systems, and has operated under the radar of global security analysts until 2018.
This group led by a man named Rueben also known as Ben, operationalized use of hackers from other threat groups with use of Grapzone’s leadership for the toughest targets around East Africa. With his leadership, the group started to expand to Central Africa, attempting to beat SilentCards threat-group in expansion around the area.
One of the exceptions OnNet CTI analysts noted with this group, was use of financiers who joined and injected money into the group in order to get dividends as if they were directors. Obliquely, Forkbombo group operated like a company or rather a cooperate entity.
With Forkbombo gone, OnNet collected intelligence on several groups as they broke up and mutated in 2019 than observed before in East African Cyber Threat Intelligence.
The newest group which we observed breaking out of SilentCards is called “The Consultants.” At the top of their target list are Government Financial Systems.
As these groups grow and mutate, resilient prevention capabilities are required to stop and evict them.
Senior members of the Forkbombo group are still behind bars, while they still have charges in other countries around East Africa for several cyber heists conducted over the years.
Kenya Insights allows guest blogging, if you want to be published on Kenya’s most authoritative and accurate blog, have an expose, news TIPS, story angles, human interest stories, drop us an email on [email protected] or via Telegram
-

 News2 weeks ago
News2 weeks agoTHE FIRM IN THE DOCK: How Kaplan and Stratton Became the Most Scrutinised Law Firm in Kenya
-

 Investigations2 weeks ago
Investigations2 weeks agoMulti-Million Dollar Fraud: Three Kenyans Face US Extradition in Massive Cybercrime Conspiracy
-

 Economy2 weeks ago
Economy2 weeks agoIran Demands Arrest, Prosecution Of Kenya’s Cup of Joe Director Director Over Sh2.6 Billion Tea Fraud
-

 Grapevine1 week ago
Grapevine1 week agoA UN Director Based in Nairobi Was Deep in an Intimate Friendship With Epstein — He Even Sent Her a Sex Toy
-

 Business2 weeks ago
Business2 weeks agoA Farm in Kenya’s Rift Valley Ignites a National Reckoning With Israeli Investment
-

 Arts & Culture2 weeks ago
Arts & Culture2 weeks agoWhen Lent and Ramadan Meet: Christians and Muslims Start Their Fasting Season Together
-

 Business2 weeks ago
Business2 weeks agoKPC IPO Set To Flop Ahead Of Deadline, Here’s The Experts’ Take
-

 Politics2 weeks ago
Politics2 weeks agoPresident Ruto and Uhuru Reportedly Gets In A Heated Argument In A Closed-Door Meeting With Ethiopian PM Abiy Ahmed